“Integrator-Filescrypt" NPM Malware Uses “Cloaking” Technology to Target StandX and Uniswap Users
The Safety research team identified a new strain of NPM malware that is using Russian “cloaking” technology to evade detection and target users of popular crypto platforms Uniswap and StandX.
Executive Summary
The Safety research team identified a new strain of NPM malware that is using Russian “cloaking” technology to evade detection and target users of popular crypto platforms Uniswap and StandX. These packages, integrator-filescrypt2025, integrator-2829 and integrator-2830 employ the commercial Adspect cloaking service to distinguish between real users and security scanners. The threat actors then serve malicious secondary payloads to real users, while giving benign packages to everyone else. The intent is to stop security tools, researchers and cloud providers from knowing what the true malicious payloads are.
Threat Actor
These three packages were published by a NPM user “dino_reborn” on November 11th. In addition, dino_reborn published four other packages in September, 2025.
Attack Infrastructure
The malware uses three key domains for its operations:
association-google[.]xyz- Primary proxy serverappprotector[.]online- C2 server that delivers the malicious secondary payloadrpc[.]adspect[.]net- Commercial cloaking service API
How does it work?
There is no install script to kick off the payload, so instead these packages must be imported into a web app that the target runs locally. The malware has multiple stages:
- The malware calls
association-google[.]xyz/adspect-proxy.phpto fingerprint the victim - The
callAdspectAPIfunction collects a detailed fingerprint of the user's browser and environment. This information is exfiltrated to the attacker's C2 server (association-google.xyz) to be processed by the cloaking engine. The exfiltrated data includes:- User-Agent string
- Full current URL (host, path, query parameters)
- Referrer URL
- Browser language
- IP address (determined server-side by the proxy)
- Various HTTP headers
- The proxy calls the Adspect API at [
https://rpc[.]adspect[.]net/v2/](<https://rpc.adspect.net/v2/>)81330cb9- f454-414c-a166-9841238cb086with the above fingerprinting data to determine if the victim is a "good" target (returnsok: true) or should see a decoy white page - If targeted, victim sees a fake Cloudflare CAPTCHA page for either uniswap or standx
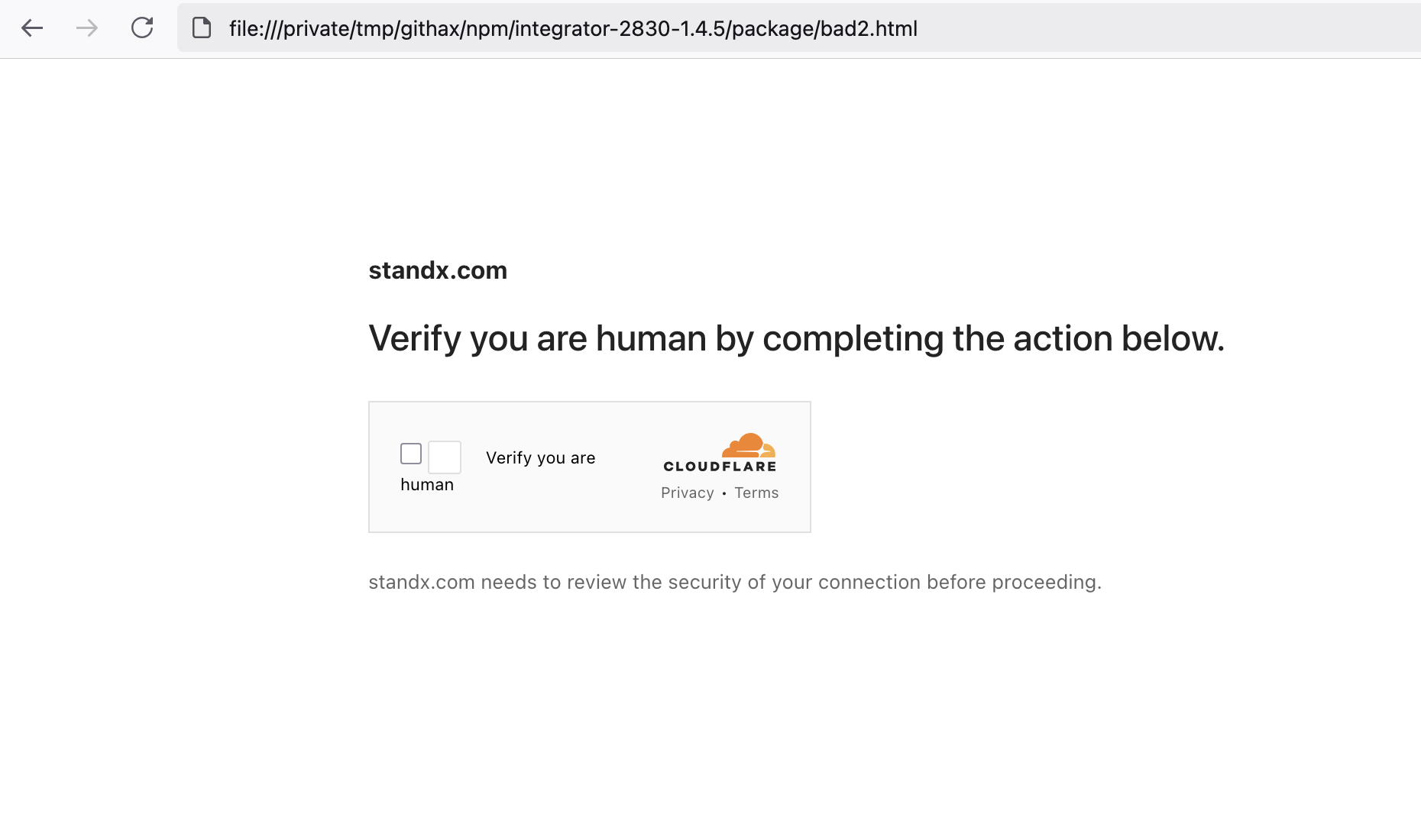
- After "solving" the CAPTCHA, the malware downloads additional payloads from
appprotector.online/adspect-file.php.
- Victim is redirected to a malicious site via
window.open(). Historically, this was a fake hardware wallet site named "Unisec"

- These fake hardware wallets were priced inexpensively to entice crypto enthusiasts to call the phone number listed on the fake site:
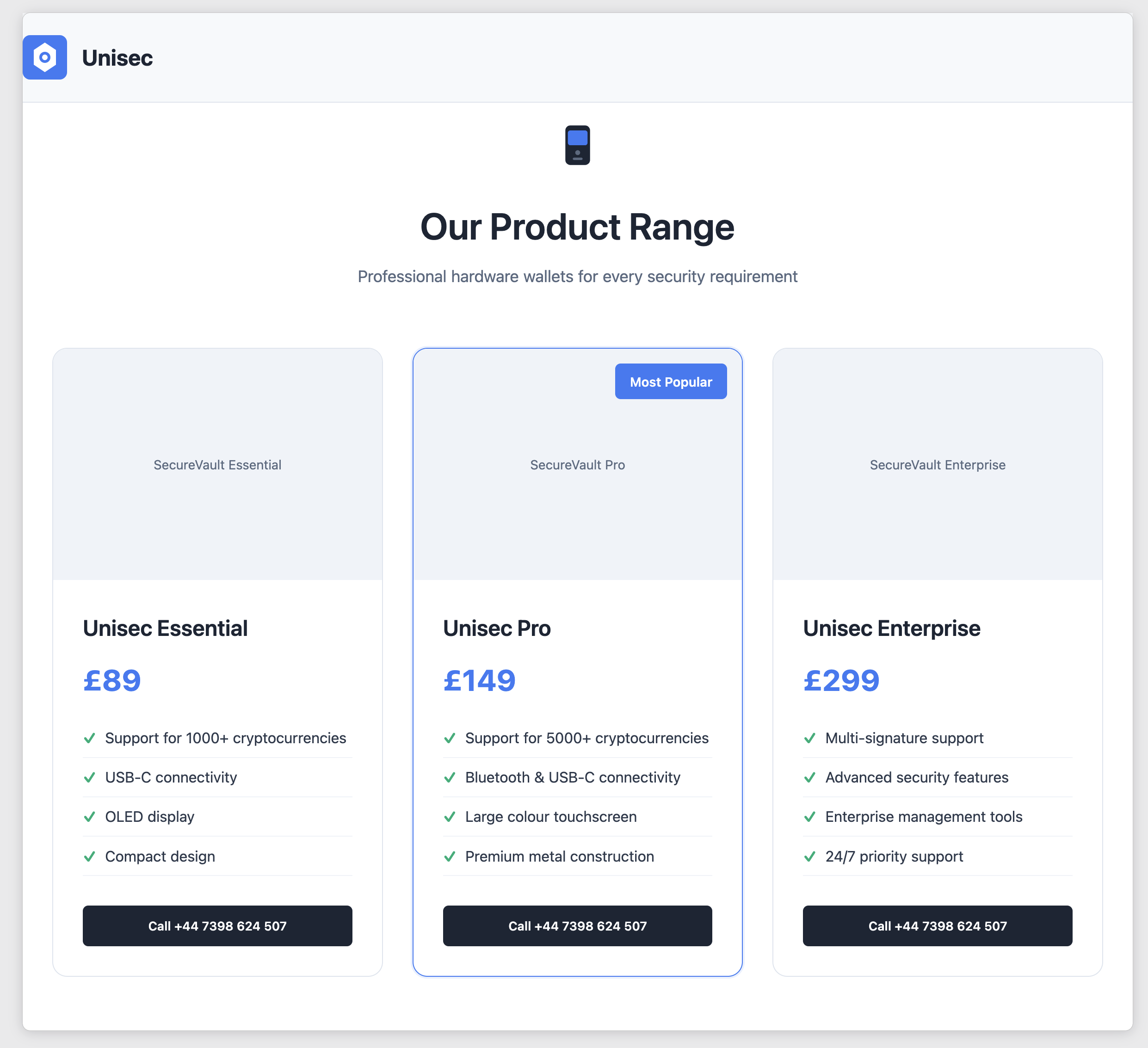
It is very probable that this final stage served up multiple fake websites, so we can't say for sure that this was the version that all victims got.
Evasion Techniques
In addition to the cloaking technology this campaign uses, it also leverages several sneaky ways to evade detection by security researchers and security scanning tools:
- Disables right-click and developer tool keyboard shortcuts
- Implements anti-debugging checks that reload the page when DevTools are detected
- Collects detailed browser fingerprints to identify security researchers
What is “cloaking”?
Ad cloaking is a deceptive technique where advertisers show different content to different visitors to hide malicious, policy-violating, or low-quality content from ad platform moderators and automated systems. Traditionally, cloaking was used for serving ads for adult content, or other products that have historically struggled to get
Cloaking works by displaying a compliant "white page" to bots and reviewers while showing a different "black page" with the actual content to human users. This can lead to click fraud and malware distribution.
Who is Adspect?
Adspect is a cloaking company based in Russia. They advertise that their customers won't get banned by Facebook, Google, Tiktok, Apple, Bing, X (Twitter), Yandex, Snapchat, Taboola, Outbrain, Google Play, App Store, and more.

In fact, the company positions its product as a "bulletproof cloaking" solution and in its FAQ section says that they don't care what you use their service for:
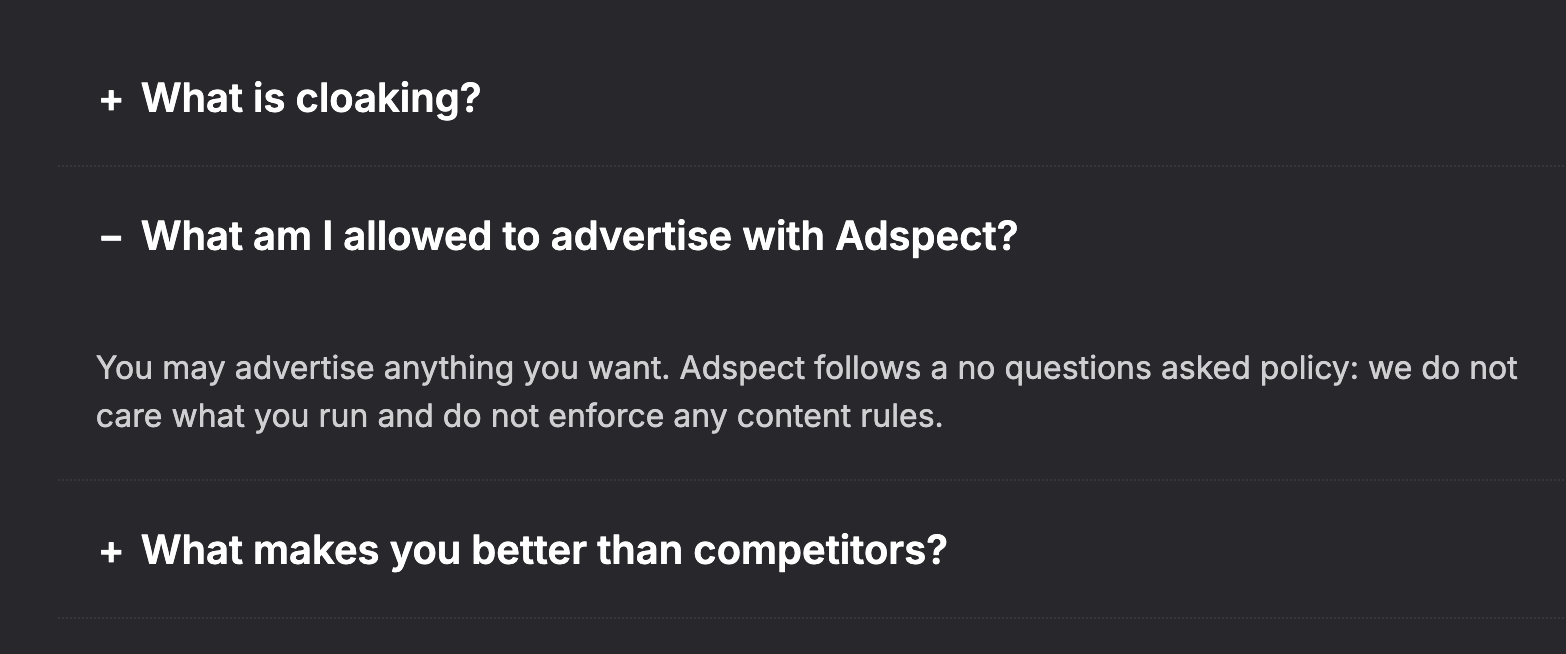
The company website says the company is headquartered in Malta, and their GitHub account says they are based in the UAE, but based on our research, the company and its employees are Russian.
Moreover, Adspect has a heavy presence on blackhatworld[.]com, which is one of the largest websites serving the grey and black market advertising ecosystem.
Our analysis and insights
After studying the NPM packages involved in this threat campaign it is our guess that these packages were part of a testing phase before the main campaign started. This theory is based on several factors including the multiple uses of "test" in the package manifest files, and that the authors didn't obfuscate the code or hide it in any other way. We don't know why the threat actor published them to the public NPM registry instead of testing them locally.
More importantly, we anticipate threat actors using cloaking technologies more as malicious package detection becomes better and more common.
Finally, we suspect that these packages were going to be used in targeted phishing or watering hole campaigns as the packages themselves don't use lifecycle install scripts. They could also be used in campaigns targeting crypto developers on platforms like LinkedIn or Reddit.
Indicators of Compromise (IOCs)
Based on our research this threat campaign has several IOCs you can look for. In particular you should be block egress in your organization to the Adspect domains, as there is no legitimate business reason for network connections to those domains.
NPM Packages - all versions:
application-phskck
applicationooks21
dsidospsodlks
integrator-2829
integrator-2830
integrator-filescrypt2025
signals-embed
URL/Domains:
association-google[.]xyz
appprotector[.]online
adspect[.]io
adspect[.]net
How can Safety help protect you from these attacks?
Traditional vulnerability scanning happens too late - after potentially malicious code is already in your system. Which means that ASPM and EDR solutions don't protect you from this type of threat.
But all is not lost, as the Safety Firewall protects develoeprs and CI pipelines proactively. Every package installation request is analyzed before reaching public repositories. Malicious, vulnerable, and policy-violating packages are automatically blocked before they can enter your systems, preventing rather than just detecting threats.Every package installation request is analyzed before reaching public repositories. Malicious, vulnerable, and policy-violating packages are automatically blocked before they can enter your systems, preventing rather than just detecting threats.Every package installation request is analyzed before reaching public repositories. Malicious, vulnerable, and policy-violating packages are automatically blocked before they can enter your systems, preventing rather than just detecting threats.
You can sign up for a free Safety account and try the Safety Firewall HERE. Feel free to reach out to me with any questions!
Let us know if this blog post helped you
I hope this blog post has helped you. Feel free to hit me up directly if you have any questions about this campaign.

Paul McCarty - Head of Research, Safety
You can find me on LinkedIn and BlueSky.







.png)

